OSFF Assembly at 38C3
Like in the previous year, we visited the Chaos Communication Congress and hosted an assembly.

Like in the previous year, we visited the Chaos Communication Congress and hosted an assembly.
Once again, we exhibited a simple demo of the LogoFAIL vulnerability, and Ahmad Fatoum from Pengutronix joined us this time to provide a demo of the Barebox bootloader featuring Snake and DOOM.

In total, we gave 4 workshops, offered 4 badges for people to discover, and had enough space to accomodate a dozen hackers. Many people visited us, being curious about what's in their laptop's firmware or how to get coreboot on their ThinkPad T480(s) laptops, which 4 of them successfully did through the help of deguard.
Projects
One of our main focuses was on laptops and mobile devices. With a handful of Ubuntu maintainers, we had a great exchange about Chromebook support in mainline Linux and distributions, such as enabling missing modules downstream as well as userland. Those require adjustments in the respective drivers. For example, mediatekdrmfb would currently break without a DisplayPort bridge being present. Such cases require careful handling in order to ship images that work well for everyone.

Close to us sat our friends at the Linux on Mobile assembly, with whom we debugged Google's bootloader and device tree and from whom we borrowed a USB-Cereal. One of the core projects is postmarketOS, a Linux based operating system for mobile devices. That includes a lot of work on firmware on bootloaders.

Over the days of hacking, we made progresss: On Arm64 platforms, such as MT8186+, we got some steps further with audio using Sound Open Firmware (SOF) for LinuxBoot. We also discovered a regression in Mesa on a Mali G57 GPU that we will report back.

Finally, to get more people started with the project, aprl and elly gave a talk on corebooting Intel-based systems, explaining what to do when porting a new board.
Workshops
On the first day, in the first workshop, participants learned about firmware images as found on modern AMD and Intel platforms, consisting of many different parts, which they could browse using Fiedka, UEFITool and various command line tools.
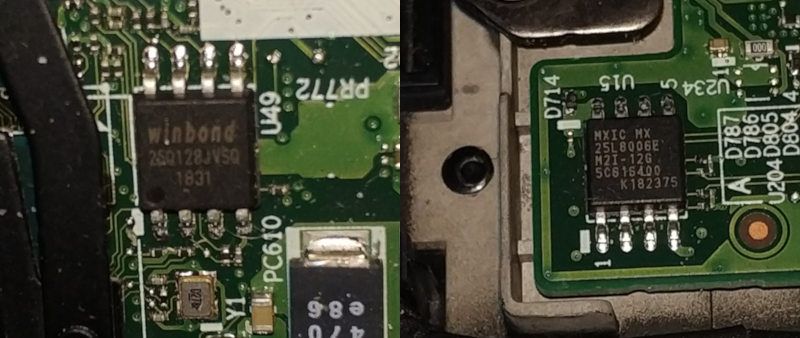
On the second day, in two consecutive workshops, we took apart firmware blobs using Ghidra and learned about various ways of following remappings in memory and dealing with peripherals, then got started with oreboot on the platform we had investigated earlier.
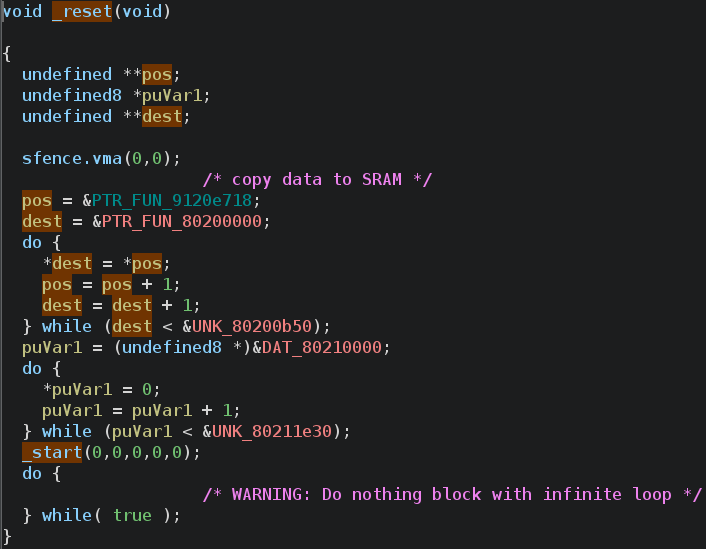
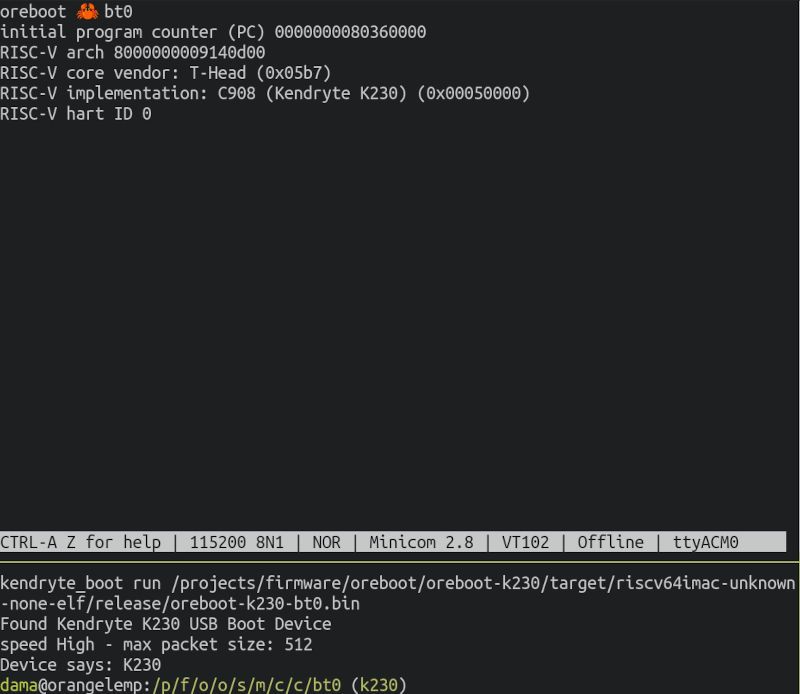
After some extra fiddling, we got the first output from a Canaan K230 SoC.

Following up on ideas from LinuxBoot and the earlier workshop on firmware images, we looked at ways of modifying UEFI firmware on laptops on the third day in the last workshop, using the ThinkPad X270 as an example. With Fiedka, we could remove unnecessary UEFI binaries, and using utk from the Fiano suite of tools, we put a Linux kernel in flash booting up within 3 seconds, finishing up with a demo of running mpv via cpu to play a video on the target device.

In conclusion, we had a wonderful experience with lots of fun and many people joining in. We look forward to the 39th Chaos Communication Congress at the end of this year and the upcoming FOSDEM, where we will be hosting a stand showcasing coreboot, flashprog and other firmware projects.